
AWS security best practices to protect your cloud architecture

Summary
In this guide, you will learn:
- The importance of AWS security as a foundational pillar in the AWS Well-Architected Framework
- Key AWS security best practices: IAM, data encryption, and VPC network protection
- How AWS services like GuardDuty provide continuous threat detection
- The use of Miro’s diagramming tools and AWS templates for secure cloud architectures
- How Miro integrates with AWS Well-Architected Tool for collaborative risk management
- The value of automated security responses and real-time collaboration for strong AWS security
Whether you’re running a small application or managing a large-scale enterprise system on Amazon Web Services (AWS), keeping your cloud environment secure should be your top priority. Without solid security measures, your infrastructure could be vulnerable to cyber threats, compliance risks, or costly downtime.
The good news? AWS provides a powerful set of tools and techniques to help protect your data, applications, and workloads. In this article, we’ll walk you through the essential AWS security best practices you should implement to minimize risks, maintain compliance, and protect your infrastructure.
AWS cloud architecture
Drag and drop AWS shapes, save time with AWS templates, and easily build technical diagrams.
What is AWS security?
Designing an AWS cloud architecture is a lot like building a house. Without a solid foundation, it doesn’t matter how much time and effort you put into decorating—the whole structure simply won’t hold up.
To help users build a strong foundation for their cloud systems, AWS introduced the Well-Architected Framework—a collection of best practices for designing and managing workloads in AWS. The Framework revolves around six pillars:
- Operational excellence
- Reliability
- Performance efficiency
- Cost optimization
- Sustainability
- Security
The security pillar is all about protecting your data, systems, and assets while making the most out of AWS cloud technologies. AWS offers plenty of features and tools to support this pillar and enable you to safeguard your cloud workloads.
Shared Responsibility Model 101
Security on AWS is based on a Shared Responsibility Model, under which you (the customer) and AWS work together to ensure the highest possible level of security for your systems.
AWS is in charge of the “Security of the Cloud”—it protects the infrastructure that powers all AWS services, including:
- Software: Compute, storage, database, and networking services that support your workloads
- Hardware/AWS Global Infrastructure: Physical infrastructure, such as servers and data centers, organized into AWS Regions and Availability Zones
You (the customer) handle the “Security in the Cloud.” This means that it’s your duty to secure the data and apps you deploy within AWS. You do so by:
- Managing access controls
- Keeping your applications and systems up to date with security patches
- Implementing networking traffic protection
- Ensuring data integrity and authentication
Shared Responsibility Model Example
Keeping your systems secure is a team effort between you and AWS, but the workload isn’t always split evenly. The amount of work you’ll have on your plate depends on the particular AWS service you use.
Here are two examples:
AWS cloud service | Description | Your security responsibilities |
Amazon Elastic Compute Cloud (EC2) | A service that lets you rent virtual servers with different processing power, storage space, etc. You get the basic infrastructure and customize everything else, so you have more responsibilities. | • Managing the guest operating system |
Amazon S3 | A cloud storage that lets you save and retrieve all kinds of data, like photos, audio files, or videos. In this case, AWS manages the operating system and the platform. | • Managing and encrypting data |
AWS security best practices and how to implement them
AWS security best practices revolve around six key areas:
- Security foundations: Ensuring the secure operations of your workloads through constant monitoring, education, and improvement
- Identity and access management: Controlling who can do what in the cloud
- Detection: Identifying incidents early on, before they affect your infrastructure
- Infrastructure protection: Securing the infrastructure and all its components
- Data protection: Protecting your data’s integrity and confidentiality
- Incident response: Defining processes for handling security incidents
Each of these areas involves numerous best practices, and we highlighted the nine most crucial ones to help you build a strong security foundation.
Divide workloads using different accounts
Not having clear boundaries between your AWS workloads can expose you to security issues, as managing permissions, access controls, and compliance for each workload can be chaotic.
To prevent this, you can separate workloads across different AWS accounts. Here are the benefits you can expect:
- Clear separation between workloads: For example, separating the production environment from the testing environment reduces the risk of accidental changes. Think of a hospital—the operating room is similar to a production environment because a surgeon won’t go in there to experiment with new techniques that could jeopardize the patient’s life. Experimenting is done in a lab or, in the case of AWS, in the testing environment.
- More control over compliance: Some workloads may involve processing highly sensitive data that needs to meet specific compliance requirements. Separating them helps you monitor compliance and minimize the risk of breaches. Let’s go back to our hospital example—the operating room has strict rules, where the environment needs to be sterile and the staff scrubbed and gowned. It would be impossible to maintain these protocols if the OR, emergency room, and labs were all in a single space.
To separate workloads and manage them with ease, you can use:
- AWS Organizations: It allows you to create and manage accounts, allocate resources, and apply policies.
- AWS Control Tower: It lets you set up and govern a secure multi-account AWS environment.
Keep up-to-date with security threats and recommendations
Security threats constantly evolve, and if you don’t stay on top of them, your system could be at risk. That’s why it’s essential to remain vigilant and monitor for any unusual activity.
One way to keep track of emerging threats is to check the Common Vulnerabilities and Exposures (CVE) List, which contains information on all publicly disclosed security vulnerabilities. In practice, however, keeping up with every new threat that comes up can be overwhelming—most of the time, only dedicated security organizations have the resources to monitor them all.
To protect your cloud systems from threats, rely on the following services:
- AWS Managed Services (AMS): This suite of AWS services helps you operate more efficiently and securely. AMS has an underlying continuous learning mechanism that analyzes workloads and pipelines with changing security policies in mind, enabling you to catch any threat early on.
- AWS Shield: It automatically detects and defends against Denial of Service (DoS) attacks that make your app or website unavailable to end users.
To make sure your security measures are at the highest possible level, monitor AWS and industry security recommendations. Follow AWS updates through its Security Blog and service documentation and subscribe to news feeds from relevant sources.
Develop strong identity and access management policies
Determining who can access your resources and in what capacity is crucial to keeping your system’s security at a high level. To set these ground rules, you can use AWS Identity and Access Management (IAM), a service that lets you control access to your AWS resources.
To build strong IAM policies, focus on the following:
Security measure | Explanation |
Least-privilege permissions | Grant users only the permissions they need to complete a task to limit the chances of misuse and mistakes and restrict access to specific areas. Review these permissions as your workload or use case matures. AWS also provides a bunch of ready-made IAM policies for common use cases, making it easier to set up permissions without starting from scratch. Plus, their support docs do a great job of breaking down what permissions a service or use case needs—and why. |
Root user credentials protection | A root user is the account owner with full access to all AWS services and resources. If someone gains access to root user credentials, they can hijack the entire account. To avoid this, use the credentials only for tasks that require them, set up a strong password, and use multi-person approvals for root user sign-in. It’s also a good idea to set up alerts whenever root credentials are used. |
Multi-factor authentication | Multi-factor authentication (MFA) adds an extra layer of security by requiring users to enter a code from their MFA device in addition to their username and password. |
Continuous monitoring | Regularly review IAM users, roles, permissions, policies, and credentials to remove those that you no longer need in your AWS account and revise your setup. |
Analyze logs centrally to simplify threat detection
In AWS, logging means writing down everything that happens in your AWS environment, including security-related events. Some of the logging happens automatically, while some occurs only if you configure it.
Depending on the complexity of your AWS architecture, you may need to analyze a bunch of logs to spot patterns and potential security threats. The more complex the architecture, the more challenging it becomes to process all the logs. One way to simplify this process is to create a centralized logging system.
There are several ways to do this, including:
- Using Amazon OpenSearch to collect and visualize logs from numerous sources
- Integrating the flow of security events and findings into a ticketing system
- Integrating security alerts into your team’s chat
- Using AWS CloudWatch to monitor all logs from a unified, real-time dashboard
- Leveraging Amazon GuardDuty to monitor your AWS accounts and workloads for malicious activity and get in-depth security insights
Classify the data within your workload and define data protection controls
Data classification is one of the most important AWS data security best practices, especially when working with highly sensitive or confidential information.
You need to understand the data your workload is processing and all relevant rules and regulations that apply to it. For example, you can group your data into these three categories:
- Publicly available data: This is the data everyone can access. Let’s think of a hospital once again—this would be the waiting room you walk into when you enter the building.
- Data for internal use: A type of data only some people can access, like people in your team. In our hospital example, this would be the break room for nurses and doctors—you can’t get in there if you’re a patient.
- Restricted data: This is highly sensitive info only a few privileged people can access. This would be the operating room—only scrubbed-up surgeons and nurses can enter it.
Once you’ve classified your data, you can set appropriate protection controls. For instance, you’ll protect restricted data with encryption.
AWS also offers resource tags you can use to “mark” data and resources within your AWS accounts based on their sensitivity. Then, you can use services like IAM or AWS Key Management Service (KMS) to:
- Manage access and permissions
- Set rules across specific accounts
- Manage and rotate encryption keys
Encrypt data at rest and in transit
Data at rest refers to the data that’s stored and not actively moving, while data in transit is the “active” data being transferred from one place to another. Encrypting both types is crucial for protecting information against unauthorized access and mishandling.
AWS offers multiple services and features that simplify and automate data encryption and key management:
- AWS Key Management Service (KMS): It lets you create and control encryption keys. You can control and rotate the keys yourself or have AWS manage them for extra convenience.
- AWS CloudHSM: The service allows you to access, manage, and protect your encryption keys through hardware security modules (HSMs). Think of HSMs as impenetrable high-security vaults where you can stash your encryption keys without worrying about unauthorized access.
- AWS Certificate Manager (ACM): This tool lets you provision and manage SSL/TLS certificates for end-to-end transit encryption. It lets you securely stop traffic to your website or app or protect communication between resources within your private network.
Use Amazon Virtual Private Cloud (VPC)
Amazon VPC is a virtual network that lets you run your resources in a secure environment. It’s logically isolated from other virtual networks in AWS, much like a private part of a beach, where you can set your own rules and choose who can access it. This isolation protects your infrastructure from external threats.
You control components of your VPC such as:
Component | Definition |
Subnets | Subnets are one or more IP address ranges within your VPC. Your VPC is a city—subnets would be its neighborhoods. |
Gateways | Network, NAT, and virtual private gateways enable your VPC to communicate with other VPCs, the internet, or data centers. They are like the gates of your house. |
Route tables | They represent a set of rules that direct network traffic. Think of them as police officers who regulate traffic at an intersection. |
Develop incident management plans
You and your team need to have a plan in place to deal with and recover from incidents as efficiently as possible. The content of your incident management plan depends on your specific circumstances, but here are some tips to help you get started:
- Consider relevant compliance requirements: For example, if you’re running a workload with European personally identifiable information data, your plan should account for potential data residency issues in line with the EU General Data Protection Regulation (GDPR).
- Identify key personnel: Create a list of internal personnel whose help you may need to respond to and recover from an incident. Do the same for external personnel—for example, you may need specialist teams to properly handle a particular issue.
- Understand who will run the incident: Depending on your organization, the workload owner could be in charge of resolving the incident. If there are multiple teams or parties involved, you can build a RACI (responsible, accountable, consulted, informed) model to assign roles and responsibilities.
- Document relevant tools and processes: Think of all potential incidents you could be exposed to and document how you’ll handle them. Consider how you’ll communicate with your team and update each other on the progress of active incidents.
- Categorize incidents: Classify incidents according to severity to set your priorities straight. For example, you can use the standard high-, medium-, and low-risk classification.
Use a diagramming tool
While diagramming tools aren’t directly related to AWS security, they can be an excellent addition to your processes because they can help you:
- Visualize your entire AWS architecture
- Understand security components at a granular level
- Identify vulnerabilities and places that require additional security layers
- Spot and respond to threats early on
- Collaborate with your team in real time to manage security and respond to incidents as efficiently as possible
Miro is a perfect example of a powerful diagramming platform that lets you visualize even the most complex architectures and security components.
Design a foolproof AWS architecture with Miro
Miro is an Innovation Workspace with a robust feature set for visualizing all your work. It offers an infinite intelligent canvas you can use for all kinds of purposes, from roadmapping to prototyping and managing goals.
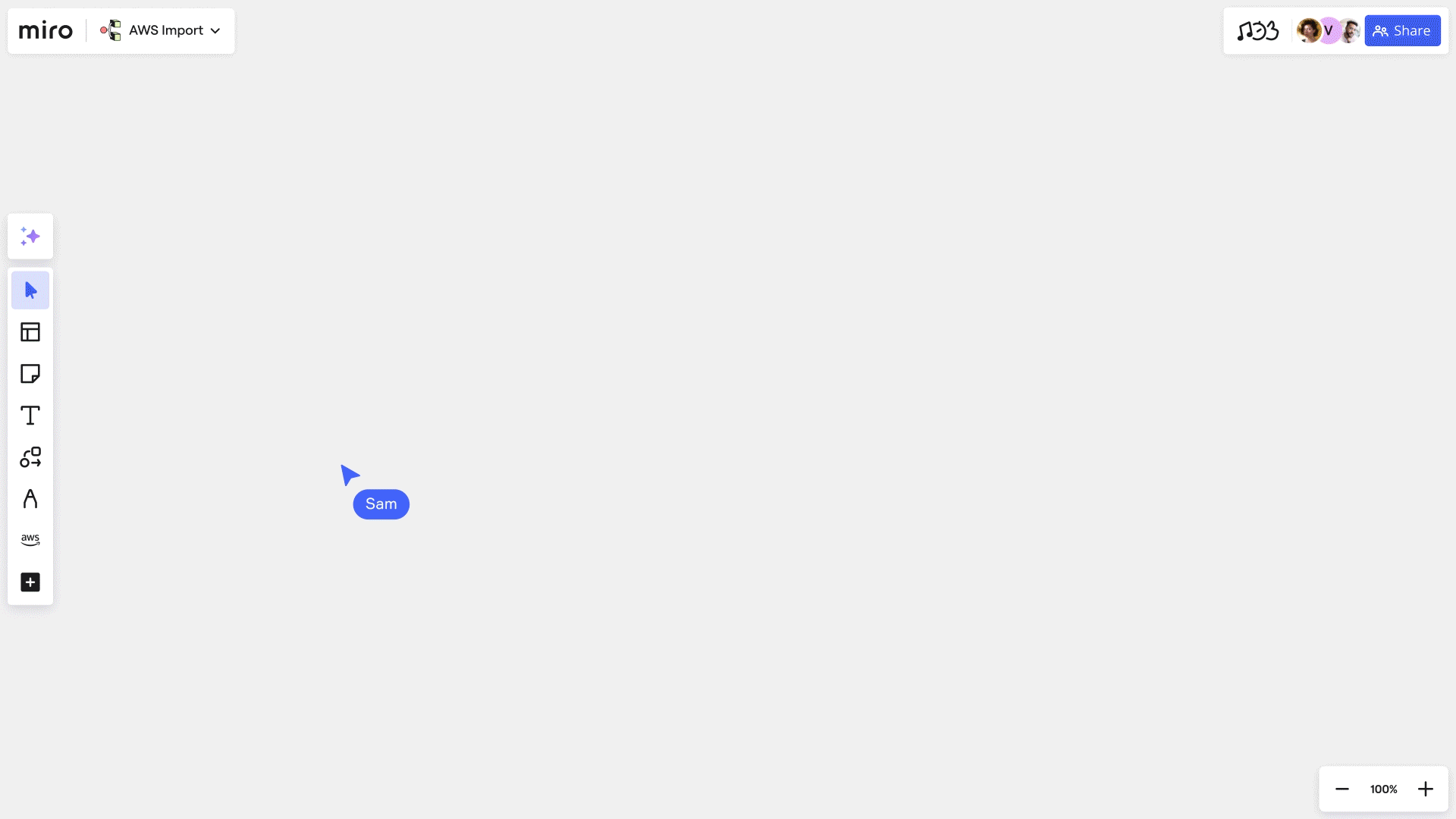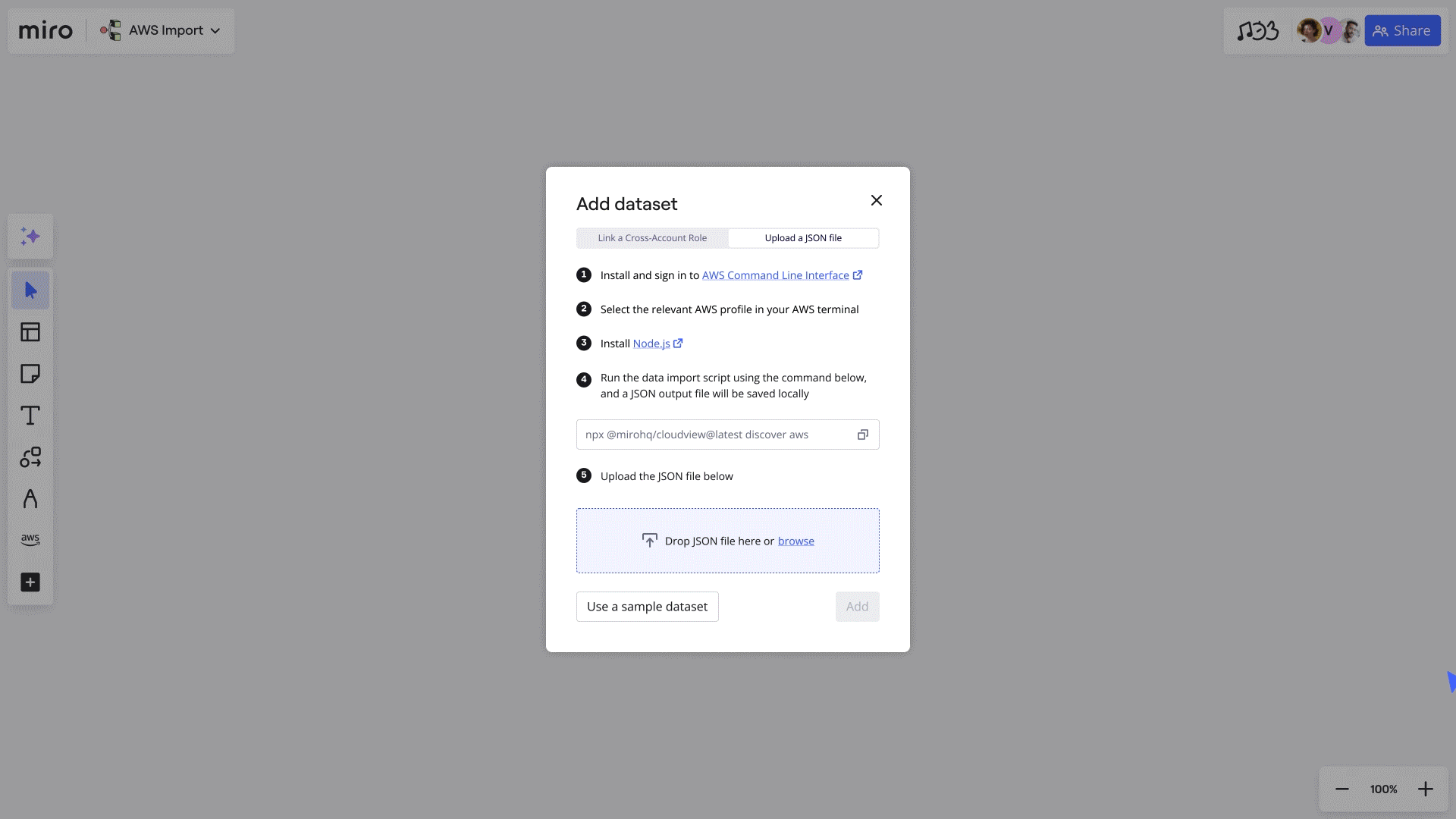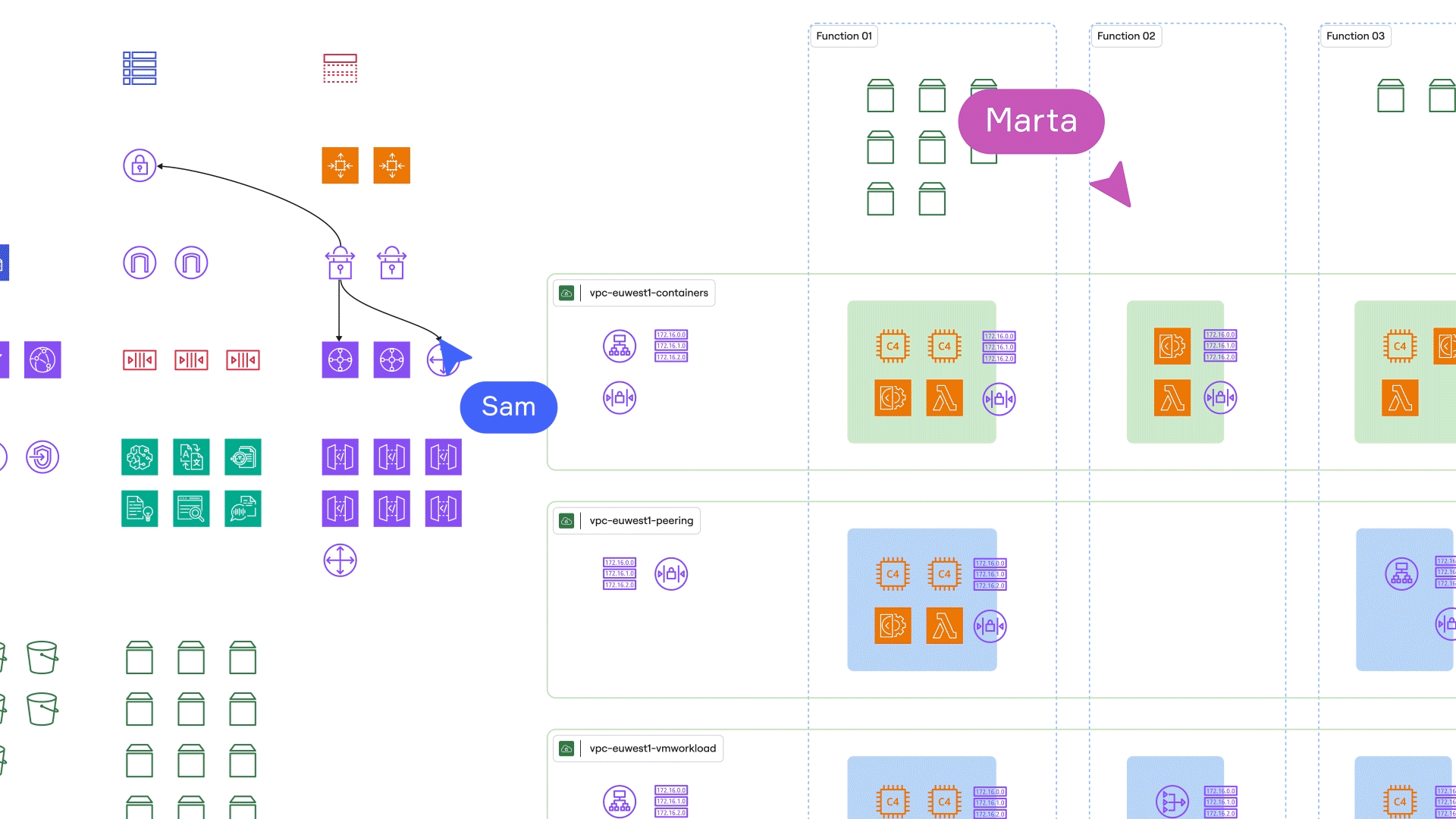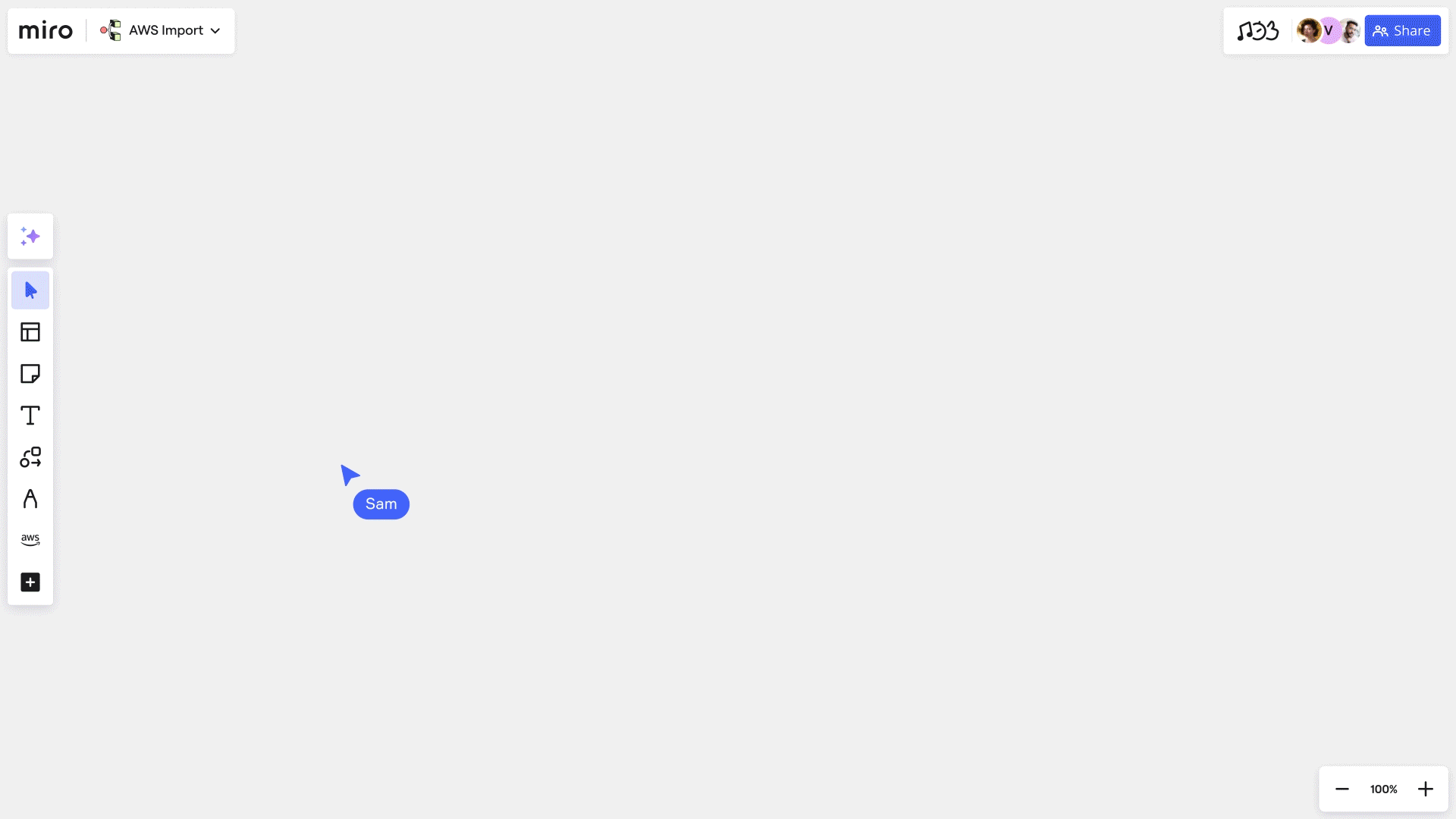
Thanks to a convenient integration with AWS, Miro is your go-to tool for mapping out your entire AWS architecture (including security components) within seconds. Having a clear visual overview of every element of your cloud setup can help you spot inefficiencies, threats, and areas of improvement to make sure security is at a high level. Some of Miro’s features can even help you automate responses to security threats and safeguard your infrastructure.
Here are some of Miro’s essential AWS architecture diagramming features:
- AWS Cloud View app: Import data directly from your AWS account and generate a diagram of your AWS infrastructure and its components.
- AWS Cost Calculator: Understand the costs of your configurations and resources, identify cost-saving opportunities, and compare costs to optimize your cloud spend.
- AWS shape pack: Unlock access to a vast library of standardized AWS icons to simplify diagramming and avoid confusion.
- Diagram focus mode: Take advantage of options such as a curated toolbar and layers to enjoy diagramming to the fullest.
- Real-time and async collaboration: Communicate with your team and relevant parties in real time to identify and quickly respond to security threats and effortlessly adjust your diagrams whenever necessary. There are also options for async collaboration for non-urgent tasks and easy remote work.
Don’t feel like creating a diagram from scratch? Use one of Miro’s diagramming templates. For instance, the Automated Security Response Template on AWS can help you improve your AWS security by automating detection and responses to threats. All templates come with a premade structure, but you can customize them to your organization’s needs.
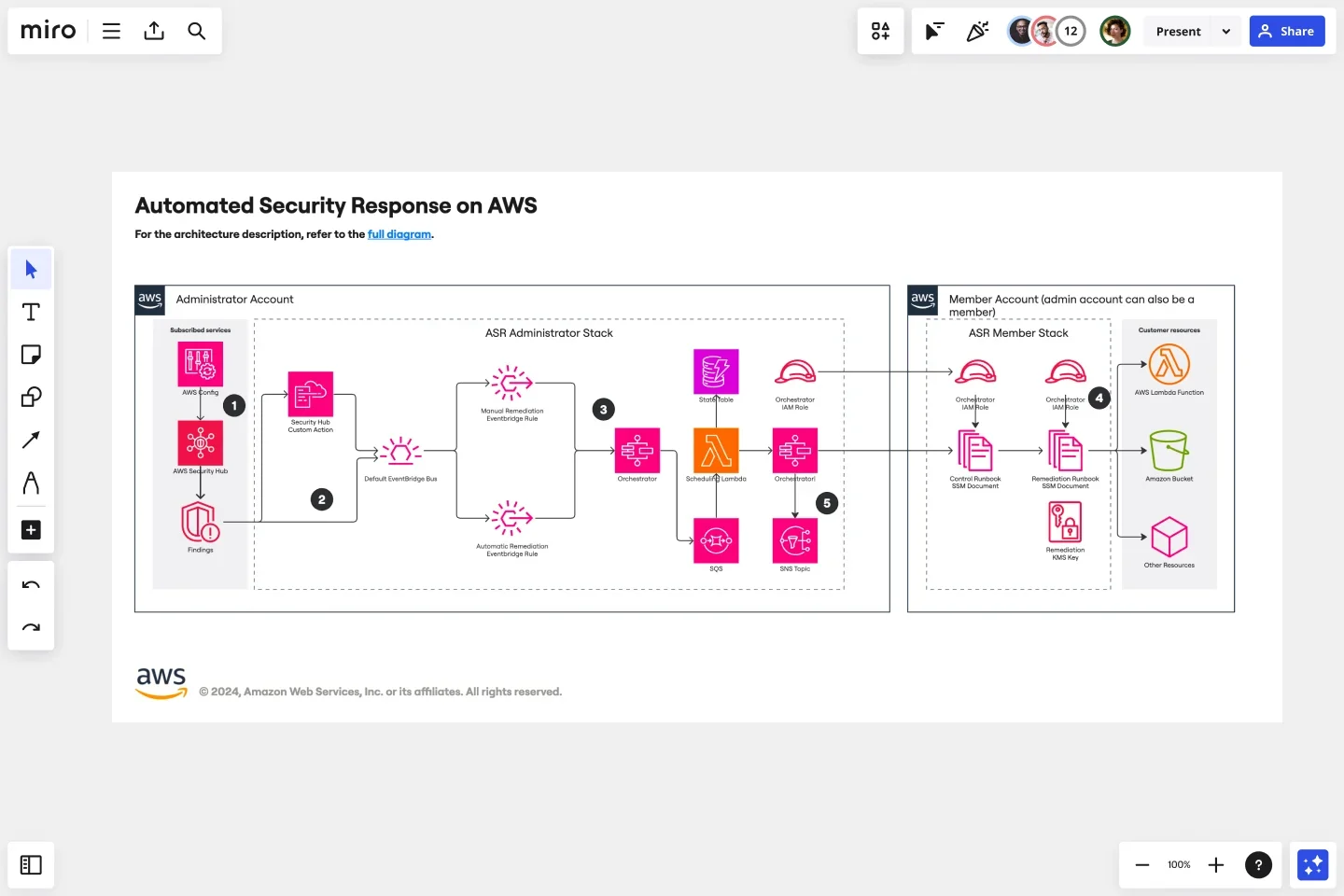
To try out Miro’s AWS features, sign up for the free Business trial and start designing a secure AWS architecture.
If you want to get a glimpse of what you can achieve with Miro, take a look at how ClickHouse, a database management company, leveraged the platform’s capabilities to accelerate feature development and boost collaboration.
We also recommend watching the AWS Well-Architected Framework webinar—this valuable resource will help you streamline and automate your architecture review process and improve collaboration.
Author: Miro Team
Last update: October 7, 2025