Google Cloud Platform (GCP) powers the world’s largest companies and applications. But this kind ubiquity also brings with it greater security risks. And guaranteeing secure code — which can extend to secure data for your organization and customers — requires more than just flipping a switch.
In this guide, we’ll walk through six practical GCP security best practices designed to help DevOps teams build safer, smarter cloud environments from day one.
What is GCP and why is security so important?
Google Cloud Platform (GCP) is the third-largest public cloud platform, behind only AWS and Microsoft Azure, with 10% of the total cloud market share.
GCP offers services for compute, storage, networking, machine learning, DevOps, and more. It powers everything from high-availability microservices and apps to massive enterprise data lakes for the world’s largest companies.
As adoption of GCP grows, so will its risk potential. Even small missteps in GCP configuration and maintenance—like leaving a storage bucket publicly accessible or over-permissions for a service account—can leave the door open to attacks.
Security on GCP isn’t optional. You need to plan for it from the start, and build your cloud environment with protection, visibility, and governance baked in at every layer.
6 GCP security best practices to protect your cloud environment
GCP gives you incredible flexibility. But with that flexibility comes responsibility. To build a secure and scalable cloud environment, DevOps teams need to establish strong security practices from the ground up.
Here’s how.
1. Secure your GCP environment with IAM and network policies
Most cloud breaches stem from simple missteps, like giving too much access or forgetting to restrict traffic. To prevent this, start with the fundamentals:
Quick definitions:
IAM (Identity and Access Management) is GCP’s tool for defining who can access which resources—and what they’re allowed to do.
- Define least-privilege access with Identity Access Management (IAM). Assign users and service accounts only the permissions they truly need. Avoid using broad roles like “Editor” or “Owner” in production.
- Use IAM Conditions. Add contextual rules like restricting access based on IP address, device type, or time of day.
- Enable multi-factor authentication (MFA) for all users. This extra layer of identity protection helps prevent account compromise.
- Segment workloads using virtual private cloud (VPCs). Create isolated environments for sensitive resources using private subnets.
- Set strict Cloud Firewall rules. Allow only required traffic between services. Deny everything else by default.
- Enable Google Cloud Armor. Protect public-facing apps from DDoS attacks and malicious traffic.
- Use VPC Service Controls. Create a security perimeter around data services like Cloud Storage and BigQuery to prevent data exfiltration.2. Protect data with encryption and key management
Data is your most valuable asset. GCP encrypts it by default, but you can—and should—take extra steps for high-sensitivity workloads.
Steps include:
- Use customer-managed encryption keys (CMEK). With Cloud KMS or Cloud HSM, you control encryption keys for services like BigQuery and Compute Engine.
- Set key rotation policies. Rotate access keys regularly to limit the impact of potential exposure.
- Protect encryption keys with IAM. Only allow trusted identities to access or manage keys.
- Control access to storage. Apply Cloud Storage bucket policies to prevent public access and enforce secure sharing.
- Enable object versioning and retention policies. These features guard against accidental deletions or overwrites.
- Secure data in transit. Ensure all communication between services, clients, and APIs is encrypted with SSL/TLS.
FYI: Cloud HSM stores keys in FIPS 140-2 Level 3–certified hardware modules for maximum security.
3. Embed security into your development pipeline
Security should be baked into every stage of the development lifecycle, not tacked on at the end. Strengthen your CI/CD workflows by:
- Securing automation with service accounts. Use short-lived tokens and least-privilege roles for tools like Cloud Build.
- Storing secrets securely. Use Secret Manager instead of hardcoding credentials in pipelines or configs.
- Running automated security scans. Scan source code, containers, and dependencies during builds.
- Enabling container analysis. Automatically scan container images in Artifact Registry for known vulnerabilities.
- Using binary authorization. Ensure only signed, verified containers are deployed to Google Kubernetes Engine (GKE) environments.
- Applying Policy-as-Code (PaC). Use Organization Policy or Config Validator to enforce deployment rules, like disallowing external IPs or enforcing required labels.
- Requiring peer reviews. Just like app code, infrastructure-as-code should go through version control and team approval.
Quick definitions:
Policy-as-Code lets you write security and compliance rules in code and apply them automatically at deployment time. Infrastructure as Code (IaC) is the practice of managing infrastructure with code for consistent, repeatable deployments.
4. Monitor and respond to threats in real time
Even the best preventive controls can fail. That’s why continuous monitoring is essential.
Here’s how to enable this:
- Enable cloud logging and cloud monitoring. Track activity across your resources and set alerts for unusual behavior, like spikes in traffic or repeated failed login attempts.
- Turn on cloud audit logs. Capture a full history of actions taken by users and services across your environment.
- Use Security Command Center (SCC). Scan your projects for misconfigurations, vulnerabilities, and compliance issues—all from a single dashboard.
- Integrate with an SIEM. Feed logs into Google Security Operations (formerly Chronicle) or third-party SIEM tools to correlate events and detect advanced threats like suspicious network traffic, compromised VM instances, or data exfiltration attempts.
- Limit admin access. Use Identity-Aware Proxy (IAP) or OS Login for just-in-time access to VM instances, which can reduce your attack surface.
Tip: Just-in-time access means ports like SSH and RDP stay closed until explicitly opened for approved, time-limited access.
5. Conduct regular audits and enforce compliance standards
Security isn’t a one-and-done project. Maintain your posture over time with structured audits and standards.
You should:
- Run quarterly internal security reviews. Check IAM roles, network configs, and resource settings.
- Use Security Command Center’s compliance reports. Monitor alignment with benchmarks like CIS security configuration guidelines, NIST frameworks to manage cybersecurity risks, or PCI-DSS to protect cardholder data.
- Label everything. Apply consistent labels—like owner, environment, or sensitivity—to improve visibility, accountability, and reporting.
- Review access controls. Identify over-permissioned users or dormant service accounts that could become entry points.
- Bring in third-party auditors. An outside perspective can uncover blind spots and validate your cloud security strategy.
Quick definition:
CIS benchmarks are security configuration guidelines developed by the Center for Internet Security to help organizations harden their systems.
6. Map your GCP architecture with Miro
Strong GCP security starts with clear visibility and close alignment between stakeholders and network professionals. The GCP Architecture Diagram Template in Miro helps you visualize your cloud environment, making it easier to spot risks, plan securely, and collaborate across teams.
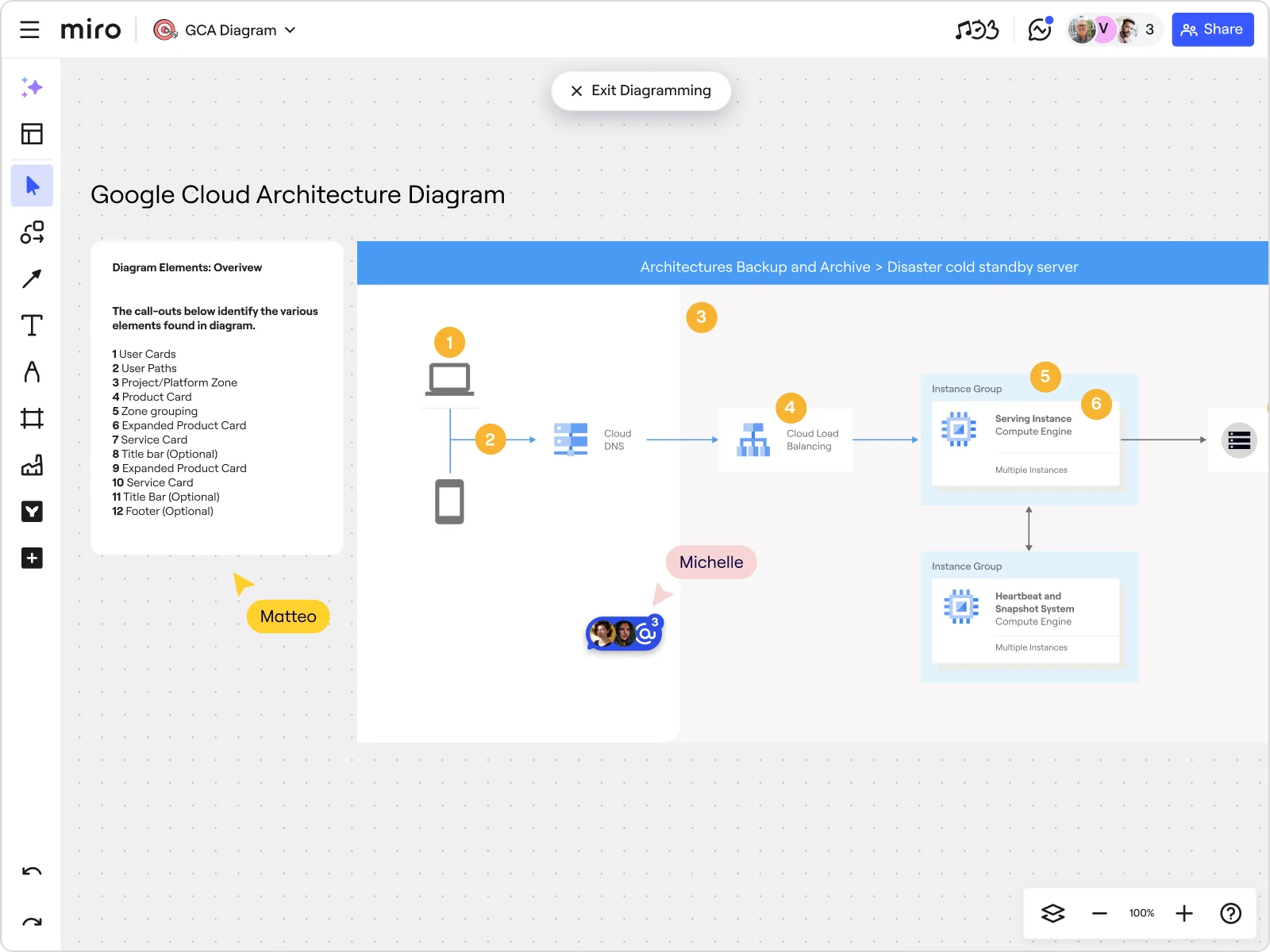
Use the template to:
- Map IAM roles, VPCs, and firewall rules
- Tag sensitive data and encryption points
- Diagram CI/CD workflows and security checks
- Document logging, alerting, and response plans
- Support audit reviews with up-to-date architecture diagrams
With built-in icons, tags, and commenting tools, Miro makes cloud security a shared, visual process by helping you document and plan your security infrastructure. Whether you’re building or auditing, Miro ensures security remains top of mind for your whole team.
Build, deploy, and maintain a secure GCP environment
Strong security starts early and never stops evolving. By building in protection at every layer, embedding it into your pipeline, and keeping a close eye on changes, your team can stay ahead of threats without skipping a beat.
And remember: the clearer your architecture, the stronger your posture. Use Miro’s GCP diagram template to bring your strategy to life—visually, collaboratively, and securely.