Securing Microsoft Azure can feel daunting. It’s an enormous platform with near endless customizations and settings. Plus, threat actors are always on the hunt for vulnerabilities, and even small missteps—like an overlooked setting—can put your entire cloud at risk. The best strategy? Start secure from day one.
Below, we’ll walk you through five security best practices every engineer team should know in order to protect their Azure environment.
But first: What is Azure and why is security so important?
Microsoft Azure is one of the world’s biggest—and most important—cloud platforms, hosting everything from virtual machines to serverless applications.
According to Microsoft, 95% of Fortune 500 companies rely on Azure in some form. This makes it a popular tool for cloud development and management, but also a high-profile target for hackers and other nefarious actors. This is why security on Azure is critical.
Common security holes in Azure deployments often involve:
- Exposed credentials (e.g., unsecured tokens or passwords)
- Misconfigured resources
- Unsecured network configurations
- Overly permissive access
Security lapses, therefore, are most commonly associated with user or management error, rather than the platform itself. Even a single oversight—like an improperly secured storage container—can escalate into a serious incident if it’s exposed by the wrong person, leading to data breaches and failed cloud migrations.
5 Azure security best practices to protect your cloud environment
To avoid security lapses, data breaches, and compromised cloud infrastructure, it’s important to follow some specific Azure security best practices. We’ll explore those below.
1. Secure your Azure environment from day one
When you first spin up Azure, it’s easy to focus on getting services up and running quickly. But before you do, you should pause to consider the security requirements for your deployment. Securing your Azure cloud architecture right from the start reduces the chances that your team will have to play security whack-a-mole in the future.
Quick definitions: Microsoft Entra ID A cloud-based service that manages user identities and permissions. Azure Security Center: A built-in platform for detecting threats and improving security across Azure. Azure Key Vault: A secure store for passwords, certificates, and cryptographic keys. Network Security Group: An Azure feature that filters inbound and outbound network traffic to and from Azure resources. It acts as a basic firewall.
At the start of your Azure deployment, focus on:
- Identity and access controls. Use Microsoft Entra ID (formerly Azure Active Directory or AAD) for authentication, enable multi-factor authentication, and stick to the principle of least privilege. Don’t forget the importance of conditional access policies in Entra ID to enforce MFA based on user risk or location.
- Network hardening. Use Network Security Groups (NSGs) to filter wanted and unwanted traffic. You can use application security groups to simplify the NSG management and improve security. Consider Azure Firewall for an extra layer of control.
- Azure Security Center. Also called Microsoft Defender for Cloud, it gives you a “Secure Score” and highlights weak spots. Use this dashboard to monitor your security performance and needs.
- Protect logins and sensitive data in Azure Key Vault. Never store credentials in code. Keep them under lock and key, secure through the Azure Key Vault. For added defense, implement protocols for key rotation, monitoring access for unusual credential use, and enabling soft delete for data and file recovery.
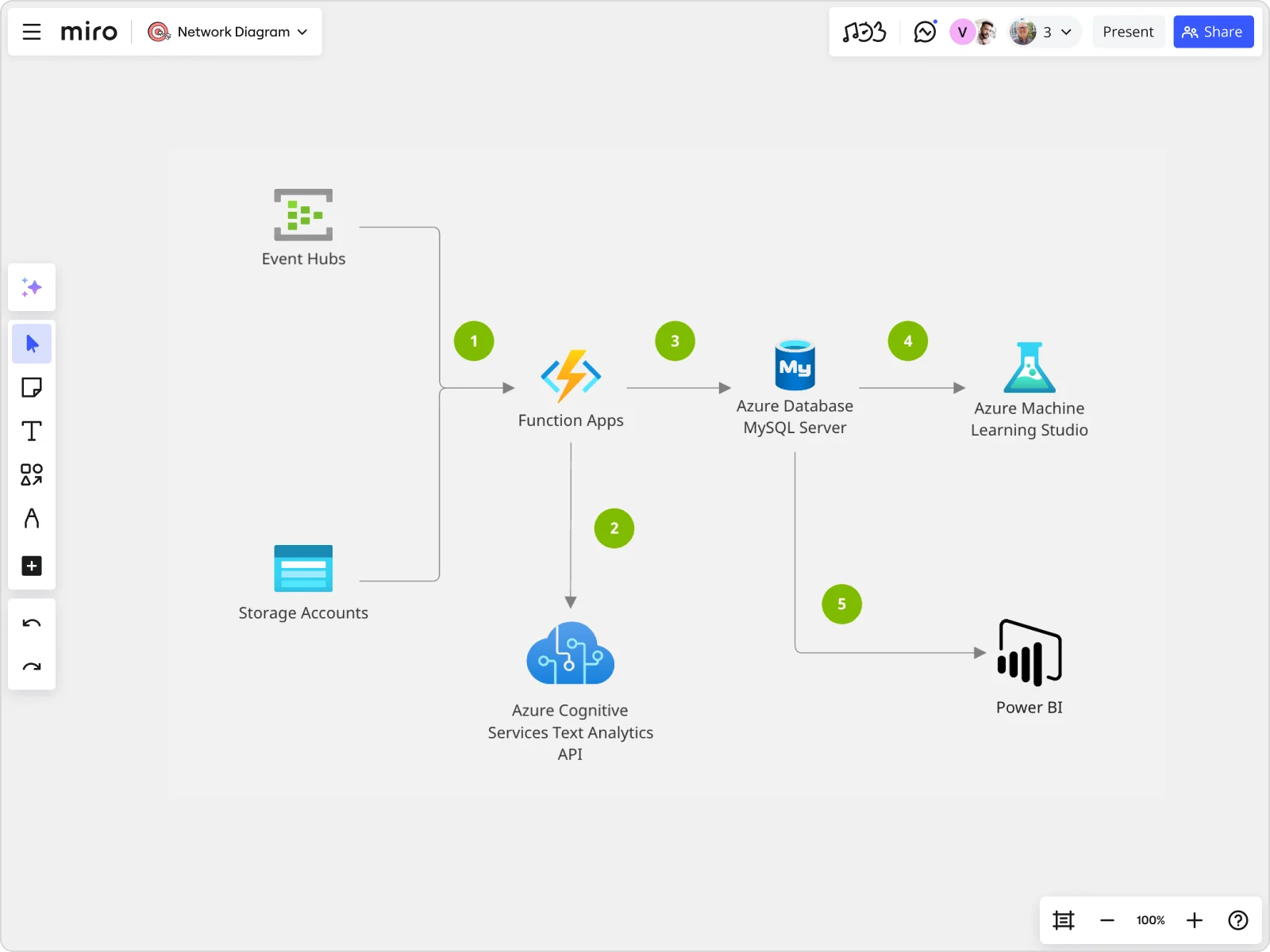
- Patch systems regularly. Set up automated OS updates to close security holes before attackers can find them.Pro tip: Need a quick overview of your Azure network set-up to help you identify possible vulnerabilities and areas that need extra security? Miro’s Azure Architecture Diagram Template helps you visualize simple to complex Azure networks, showing the steps and modules throughout our cloud architecture.
You can use Miro’s tagging, icons, commenting, and collaboration features to help with planning and auditing your security infrastructure, and maintaining alignment across teams and departments.
2. Optimize Azure DevOps for better security
Azure DevOps is the engine behind your builds and releases. Securing it reduces the risk of bad actors injecting malicious code or altering your data pipelines.
To secure Azure DevOps, you should:
- Integrate with Microsoft Entra ID. Restrict Azure DevOps to authorized users only.
- Embed security in CI/CD. Use managed identities for Azure Automation accounts to eliminate manual credential management, ensuring automated vulnerability checks are performed as part of each build.
- Use Azure Policy. This is a tool that lets you set and enforce organizational standards (such as restricting allowed VM sizes or enforcing specific configurations) and assess compliance at scale. Then you can automatically correct or block resources that don’t meet your standards.
- Apply branch policies. Mandate code reviews and approvals before merging. This practice ensures that all changes undergo peer review or lead approval before being incorporated into the main codebase, helping you catch errors and vulnerabilities before code gets shipped.
- Monitor data and process pipelines. Use Azure Monitor and audit logs to stay informed about unusual activity.
Miro’s Azure architecture diagram is useful for this stage as well, helping you sketch your data and process pipeline in detail, and tag steps that require added protections.
3. Manage resources efficiently with Azure Resource Manager
A cluttered Azure environment can lead to confusion and security blind spots. Organizing resources with Azure Resource Manager helps you maintain consistent access rules and easily track deployments.
Quick definitions:
Infrastructure as Code (IaC): The practice of managing infrastructure with code for consistent, repeatable deployments. ARM templates or Terraform: Tools that define environments in code, eliminating guesswork and manual errors.
Azure Resource Manager can help you with:
- Setting role-based access control (RBAC). Assign only the permissions each person really needs, at the resource group level.
- Implementing resource locks. Protect critical systems (like production databases) from accidental deletions or changes.
- Deploy Infrastructure as Code (IaC). Use ARM templates or Terraform to define and deploy everything in code, ensuring each environment has the right security settings from day one.
- Monitor cost and usage. Keep an eye out for spikes that may signal unauthorized activity.4. Enhance compliance with Azure tagging
Tagging is an often-overlooked security strategy that can make your life easier. By labeling each resource with fields like project name, department, or environment, you can more effectively manage and monitor large cloud environments.
You can enforce tagging through Azure Policy to ensure no one forgets to add proper labels. We recommend developing a consistent tagging taxonomy and automating tag enforcement to ensure your system doesn’t become cluttered and unstructured over time. Azure Resource Graph also allows pull reports on all your tagged (or untagged) resources, so you can spot anything out of place quickly.
Bonus: Tagging also offers better cost transparency. Breaking down resource usage and spending by tags makes it clear which projects or departments are driving resource usage, which encourages responsible management and ownership.
5. Monitor and respond to security threats in real time
Even with the strongest security measures, you still need 24/7 visibility into your Azure environment to identify and mitigate vulnerabilities and breaches before they turn into disasters.
Best practices for continuous, real-time Azure monitoring include:
- Deploying Microsoft Defender (MD) for Cloud: MD continuously scans for vulnerabilities and keeps your Secure Score current.
- Monitoring Azure Sentinel: This is a Security Information and Event Management (SIEM) tool that brings together logs from various sources to catch suspicious activity, like unusual spikes in failed sign-ins.
- Using Just-in-Time (JIT) access: Temporarily open management ports like RDP or SSH only when needed, which allows you to shrink your attack surface as needed.
For ongoing security hygiene and monitoring, Microsoft recommends using Azure Monitor to keep tabs on all logs and metrics in your cloud environments. You can also set triggers and alerts to catch anomalies and suspicious activity early.
Deploy a secure Azure environment from the start
The best protection against threats to your Azure environment is to make sure security is a priority and not an afterthought. As your cloud infrastructure grows, it becomes more complex, often leading to more vulnerabilities that bad actors can exploit.
By applying these Azure security best practices early—and using visualization tools like Miro to meticulously map areas of focus—you can create a stable and resilient cloud foundation that scales with your company.